What's New in 4.19.0.Final
Hibernate Tools
OpenShift
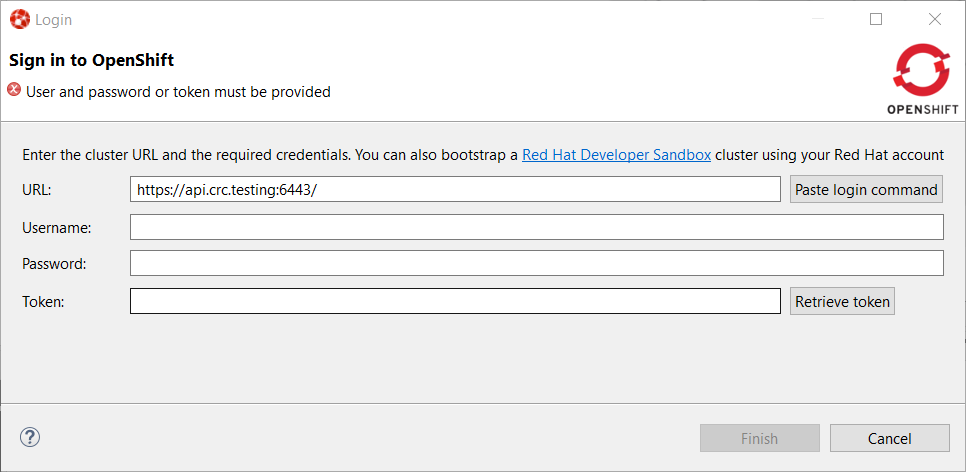
Browser based login to an OpenShift cluster
When it comes to login to a cluster, OpenShift Tools supported two different authentication mechanisms:
-
user/password
-
token
The drawback is that it does not cover clusters where a more enhanced and modern authentication infrastructure is in place. So it is now possible to login to the cluster through an embedded web browser.
In order to use it, go to the Login context menu from the Application Explorer view:
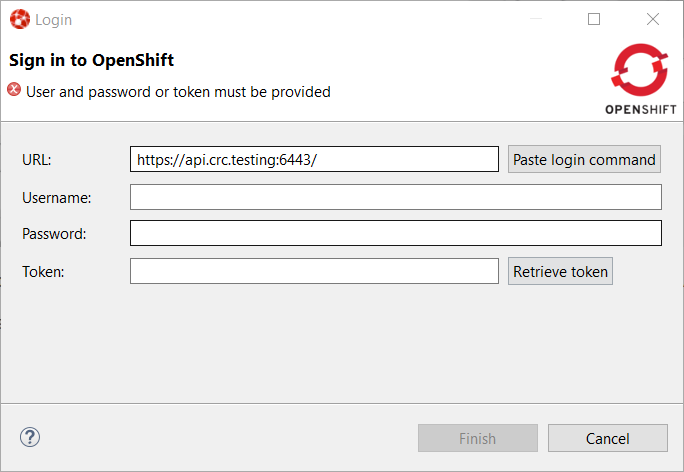
Click on the Retrieve token button and an embedded web browser will be displayed:
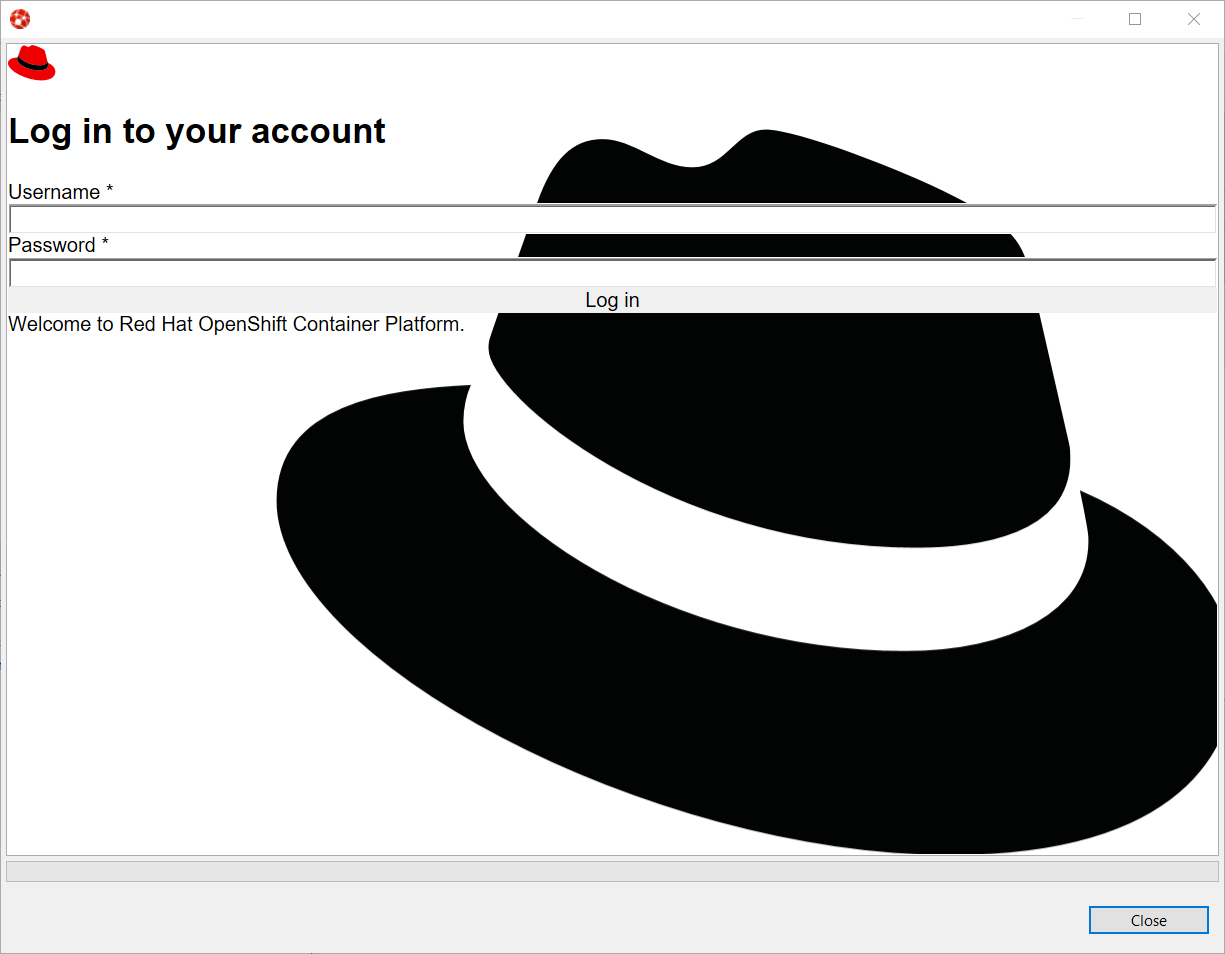
Complete the workflow until you see a page that contains Display Token:

Click on Display Token:
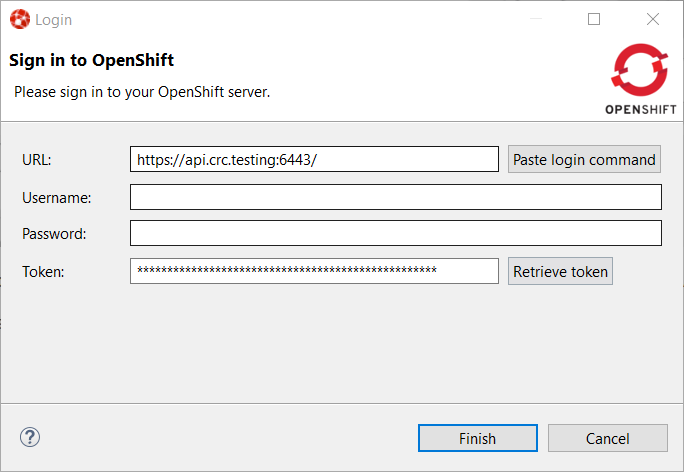
The web browser is automatically closed and you’ll notice that the retrieved token has been set in the original dialog:
Related JIRA: JBIDE-27667
Devfile registries management
Since JBoss Tools 4.18.0.Final, the preferred way of developing components is now based on devfile, which is a YAML file that describe how to build the component and if required, launch other containers with other containers. When you create a component, you need to specify a devfile that describe your component. So either you component source contains its own devfile or you need to pick a devfile that is related to your component. In the second case, OpenShift Tools supports devfile registries that contains a set of different devfiles. There is a default registry (https://github.com/odo-devfiles/registry) but you may want to have your own registries. It is now possible to add and remove registries as you want.
The registries are displayed in the OpenShift Application Explorer under the Devfile registries node:
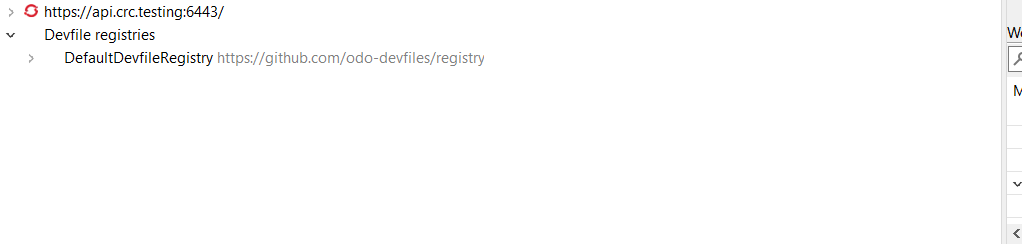
Please note that expanding the registry node will list all devfiles from that registry with a description:
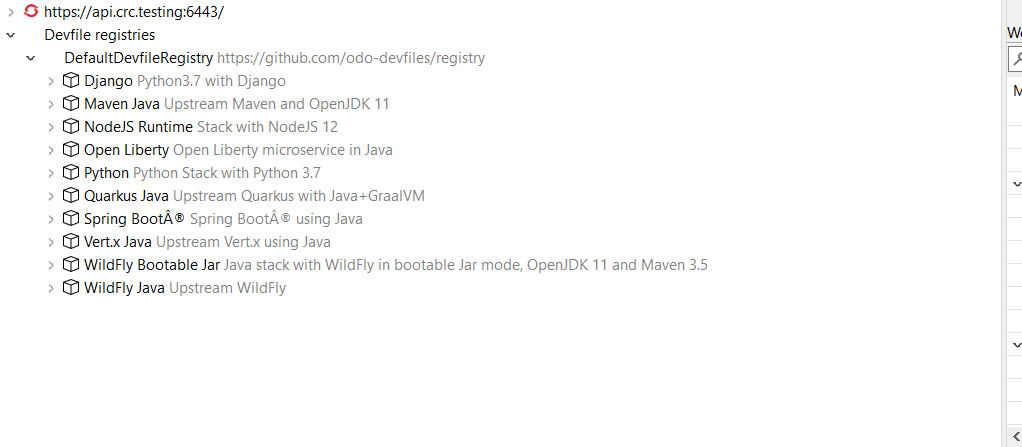
A context menu on the Devfile registries node allows you to add new registries, and on the registry node to delete it.
Related JIRA: JBIDE-27610
Devfile enhanced editing experience
Although devfile registries can provide ready-to-use devfiles, there may be some advanced cases where users need to write their own devfile. As the syntax is quite complex, the YAML editor has been completed so that to provide:
-
syntax validation
-
content assist
Related JIRA: JBIDE-27612
Support for Python based components
Python based components were supported but debugging was not possible. This released brings integration between the Eclipse debugger and the Python runtime.
Related JIRA: JBIDE-27612
Login to Developer Sandbox from the tooling
Red Hat provides an online OpenShift environment called Developer Sandbox that makes it easy for developers to build, test and deploy cloud native applications and microservices.
In order to use Developer Sandbox, you must own a Red Hat SSO account (which can be linked to social accounts like GitHub,…). Once logged in into Red Hat SSO, you will get an environment provisioned in Developer Sandbox but the first time you will try to login in to Developer Sandbox, your account needs to be verified (in order to prevent crypto miners and robots) thus you need to go through a verification phase where you will be asked to provide:
-
first your phone number and country code
-
then a verification code that you will receive on your smartphone.
So it is now possible to provision and log in to Developer Sandbox from the OpenShift tooling and connect it to the Developer Sandbox environment.
Open the OpenShift Application Explorer view (Window → Show View → Other…, enter open and double click on OpenShift Application Explorer):

Right click on the first node and select the Login context menu:
In order to provision the Developer Sandbox environment, click on the Red Hat Developer Sandbox link: a browser window will open and you will be required to login to your Red Hat SSO account:
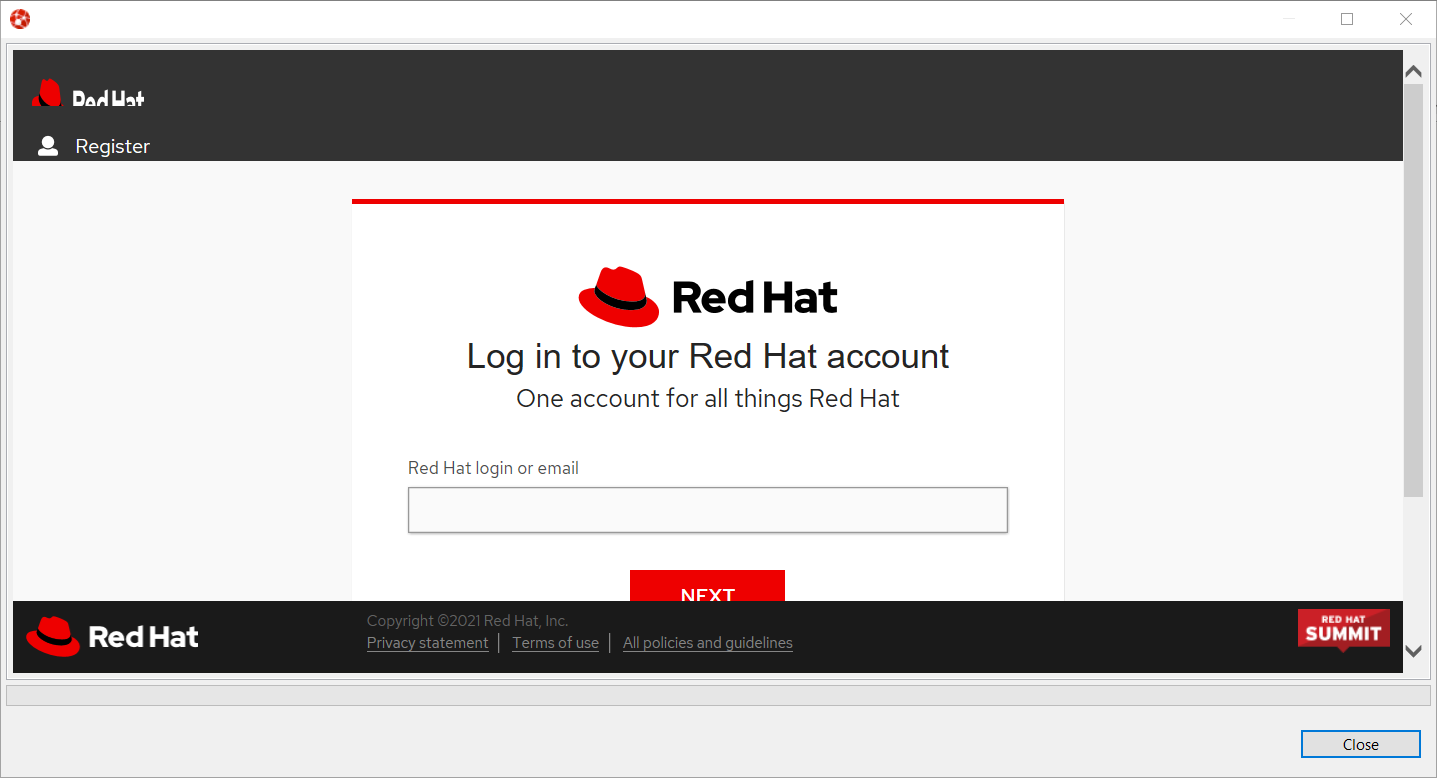
Login to your account (please note that if you don’t have a Red Hat account, you can create a new one). Once you’re logged in, you should see the following window:
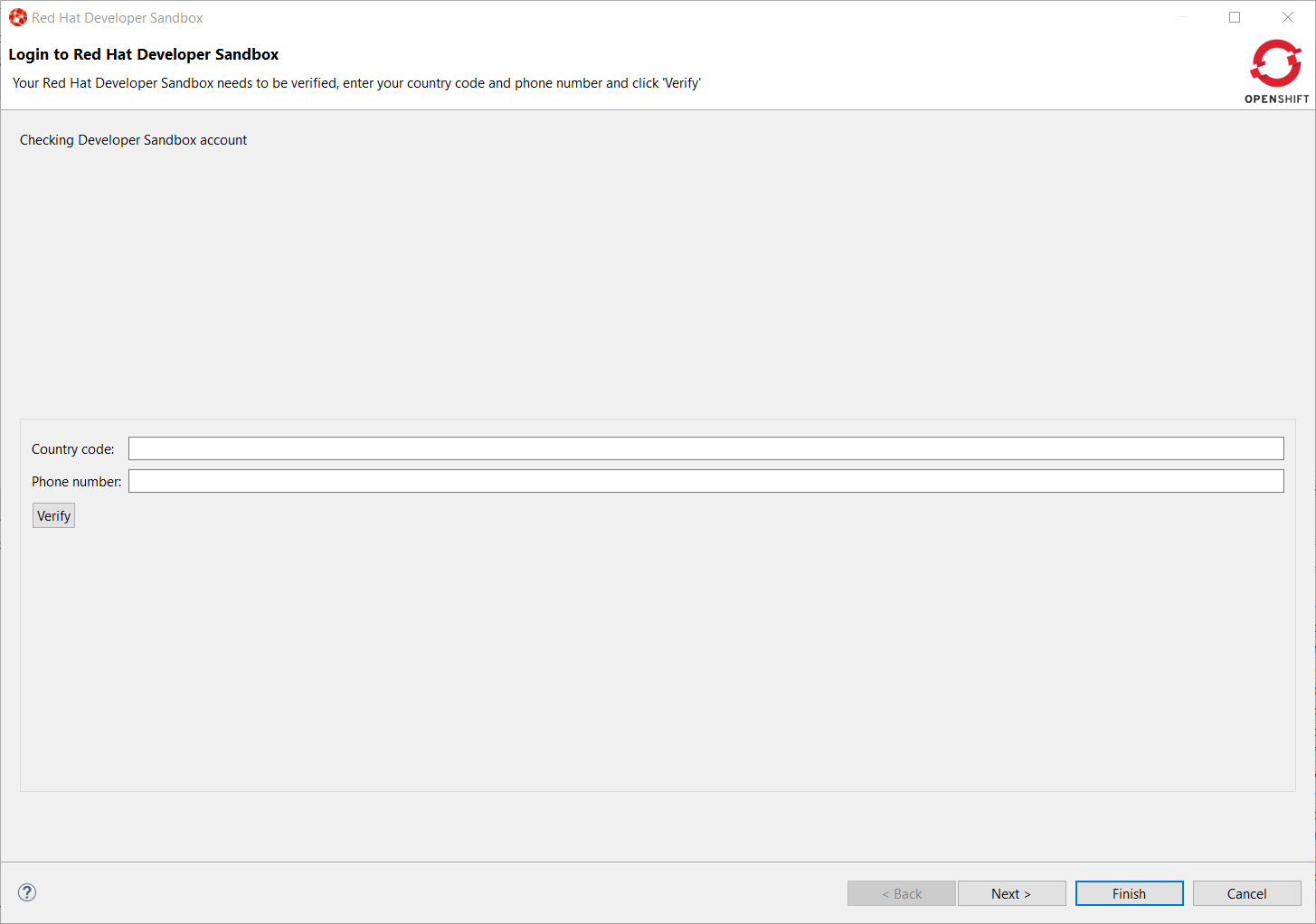
Enter your contry code (+XX) and phone number and click the Verify button:
You will be required to provide the verification code that you should have received on your phone:
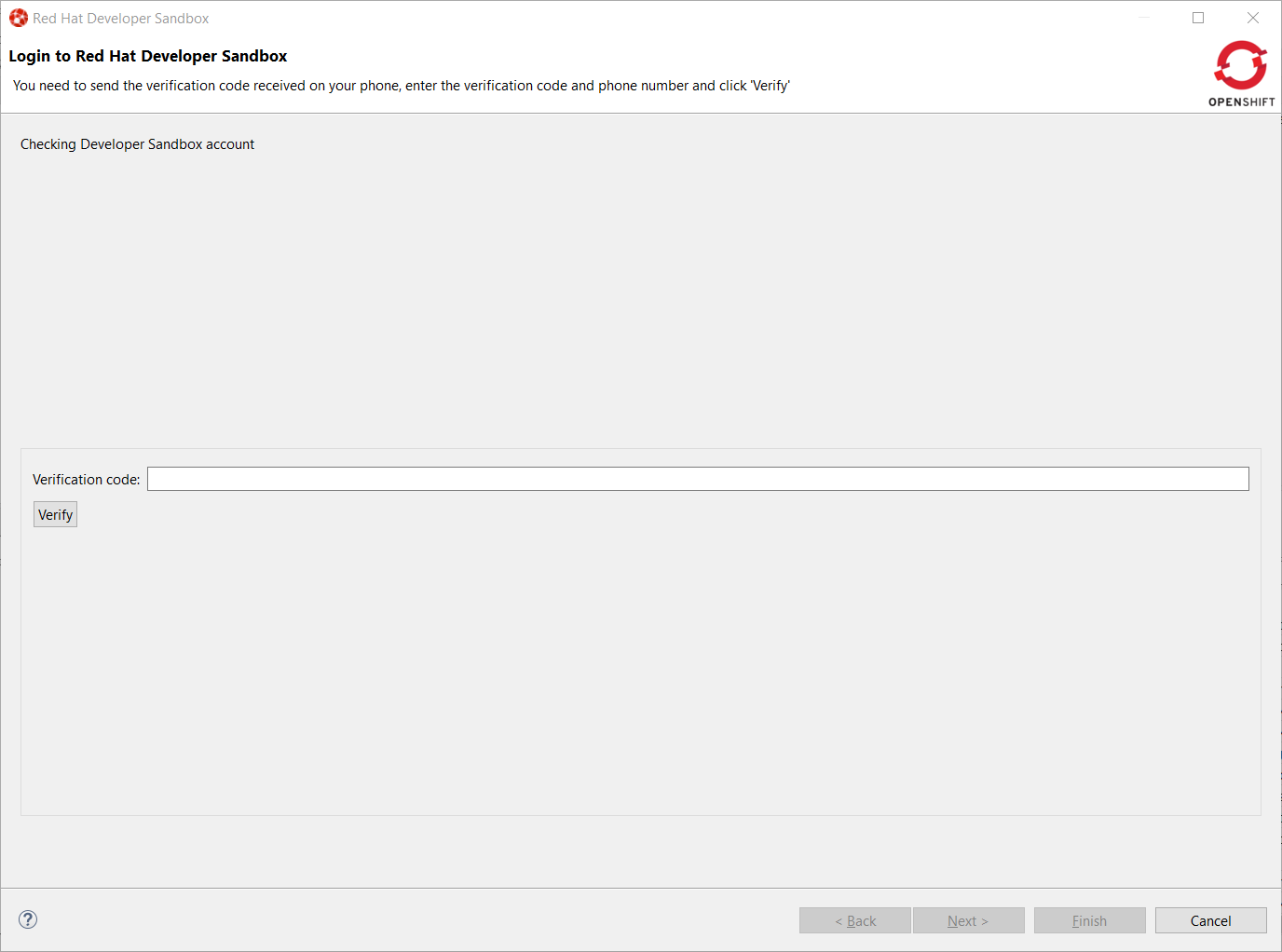
Once your Developer Sandbox environment is provisioned; you will see the following window:
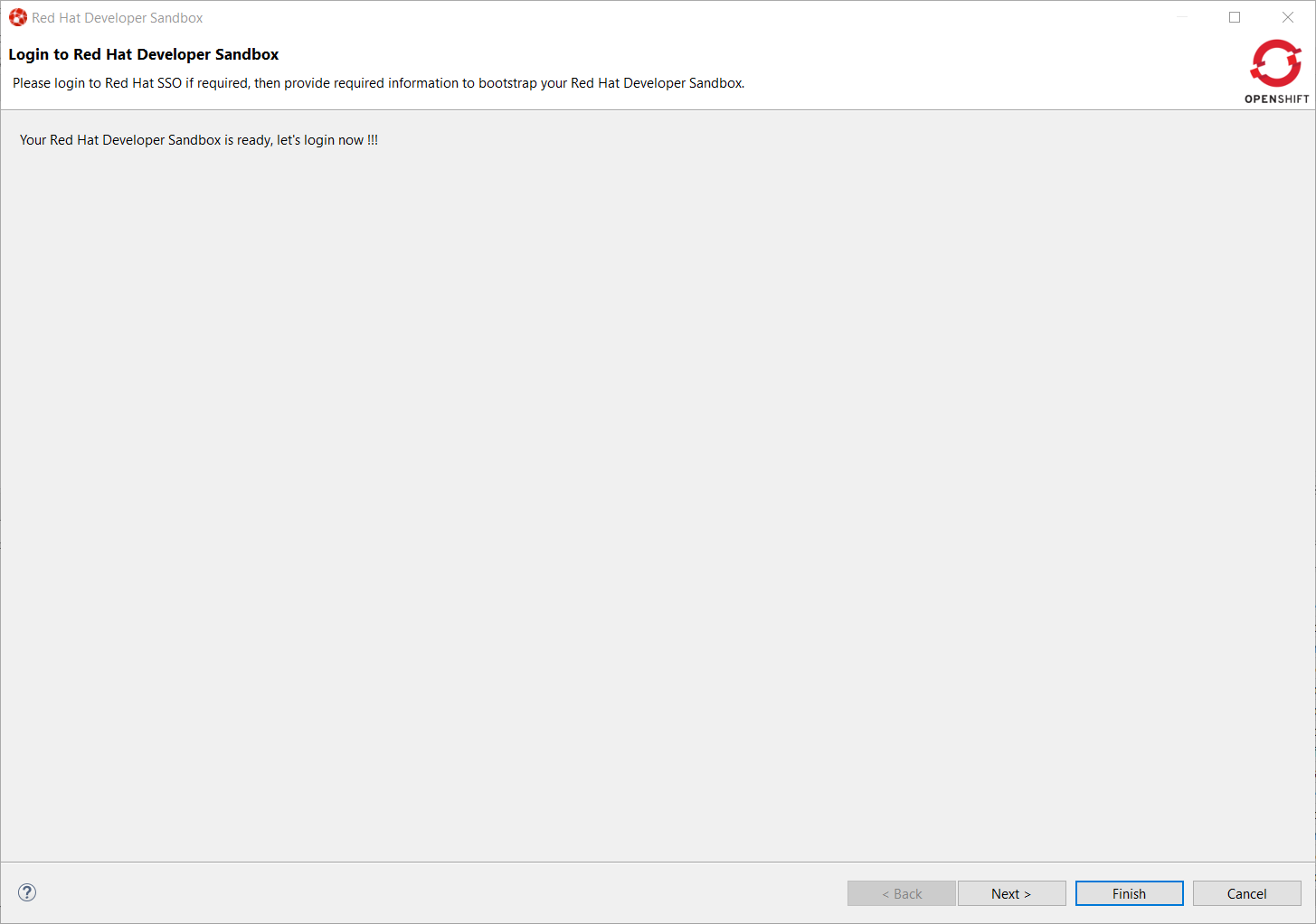
Click on the Ǹext` button to log in to your Developer Sandbox environment:
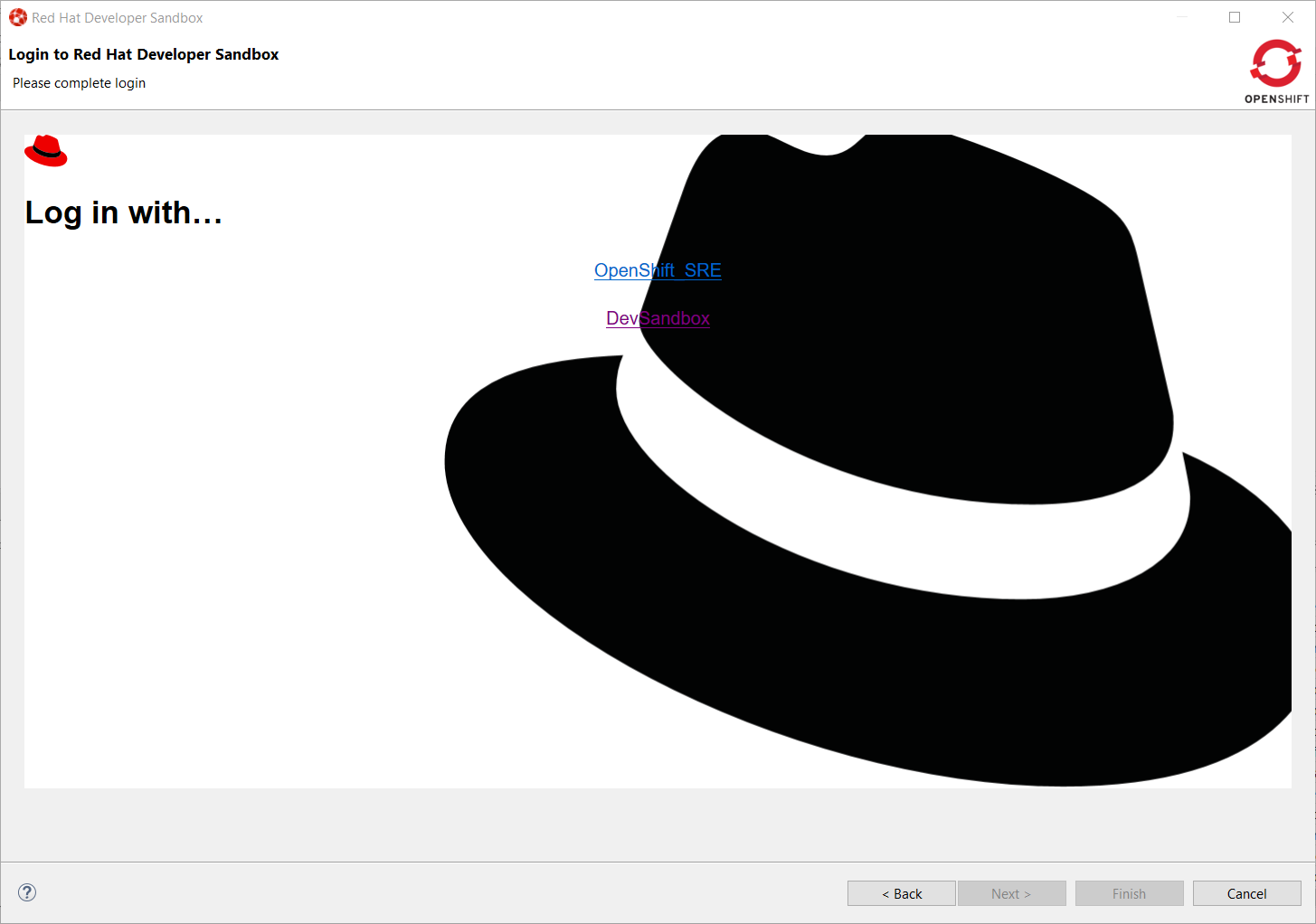
Click on the DevSandbox link and log in with the same credentials: you will see the following window:
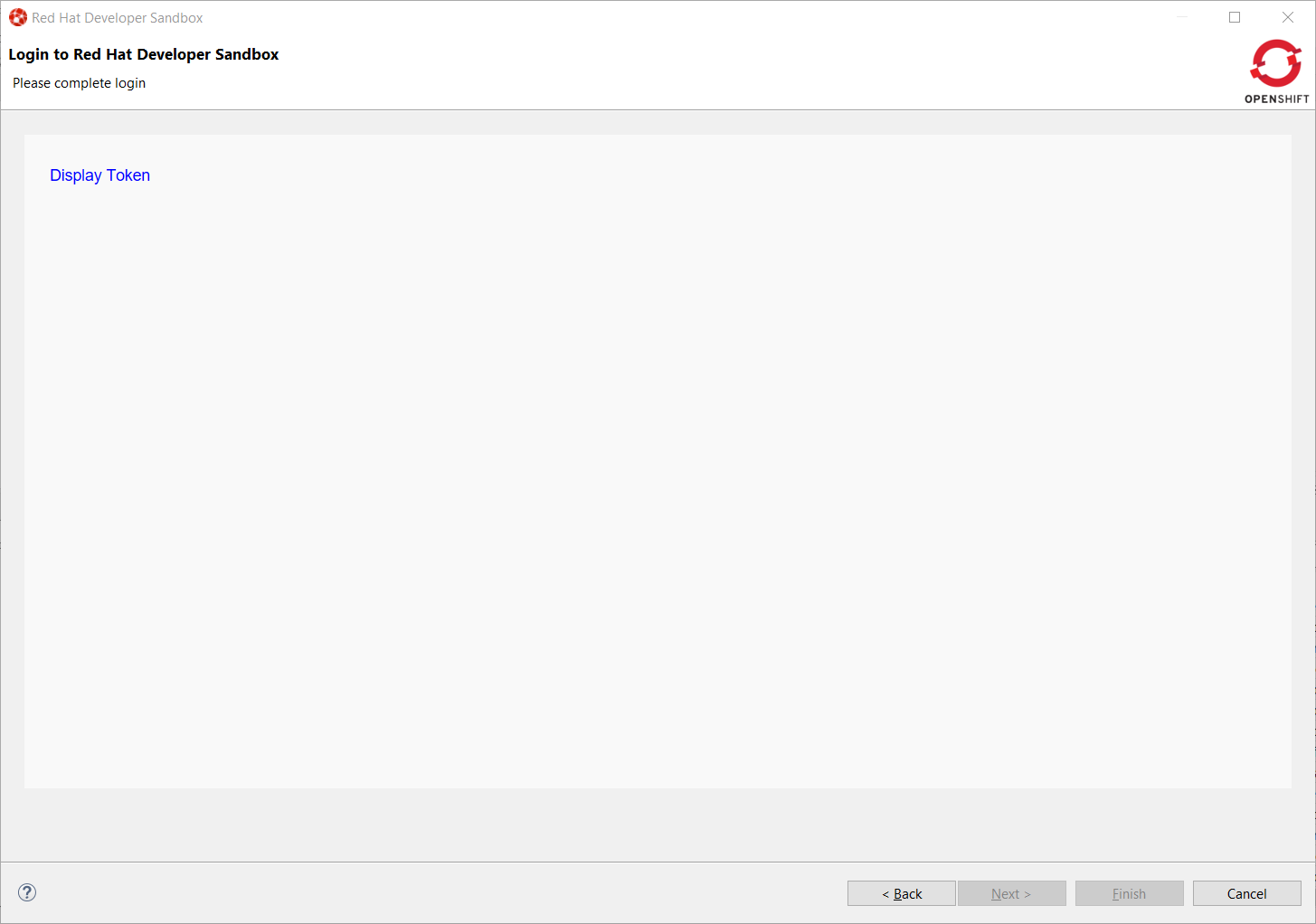
Click on the Display Token link and the click on the Finish button, you should be back to the Login wizard:
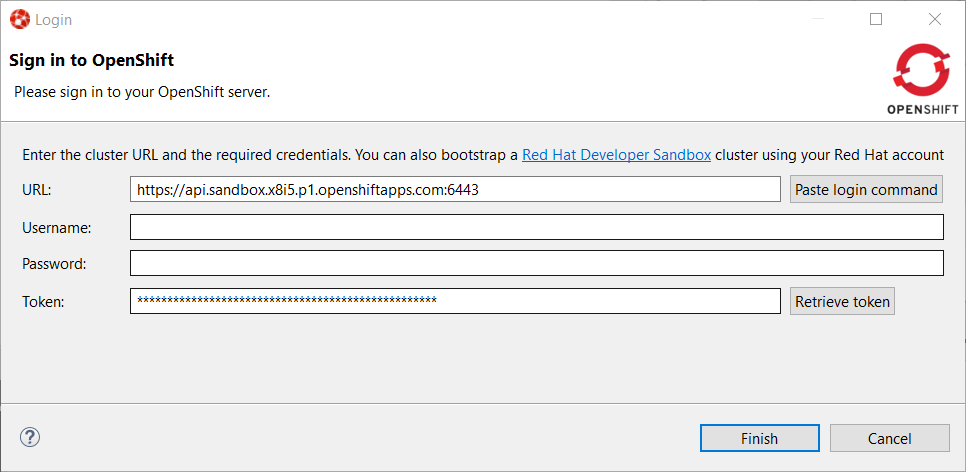
Please note that the URL and Token fields have been updated. Click the Finish button, the OpenShift Application Explorer will be updated with the Developer
Sandbox URL and if you expand it, you will see 3 namespaces/projects available for you to start playing with:
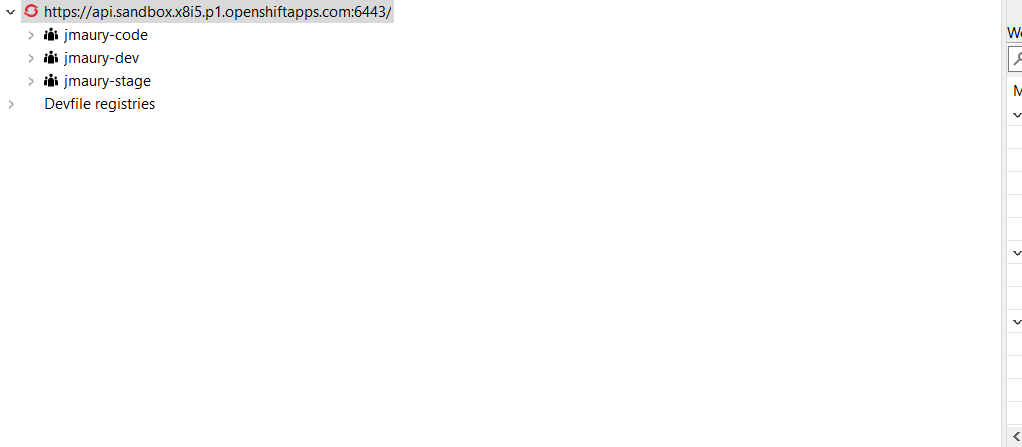
You’re now ready to work against this environment for free !!!.
Server Tools
Wildfly 23 Server Adapter
A server adapter has been added to work with Wildfly 23.
Related JIRA: JBIDE-27607
EAP 7.4 Beta Server Adapter
The server adapter has been adapted to work with EAP 7.4 Beta.
Related JIRA: JBIDE-27608